Computer attacks have become a common problem nowadays. At the same time, stopping them has become a trivial process, but not every ISP manages to implement an effective detection and mitigation system.
Often the solution chosen is "blackholing" which essentially means blocking the traffic to the IP address attacked in order to protect the other resources of the client. This method raises several problems, but the most important is given by the scenario in which several (often all) client IP addresses are attacked simultaneously. In this case, the only solution would be to restrict the traffic to all the attacked addresses and implicitly to achieve the attacker's purpose: DoS (Denial of Service).
Another problem is the detection time. Most systems use statistical-based methods and variable changes reported on average rather than peaks using NetFlow or sFlow for data collection. This implementation is inefficient at detecting most small-scale attacks and usually requires a large amount of data to make a decision, leading to very large intervals of time, sometimes on the order of tens of minutes from the start of the attack to blocking it. The only advantage of such a system is the low cost of implementation.
Providing a 99.99% uptime is not just about ensuring connectivity. When a business depends on the internet connection a congested link is as detrimental as a broken one. Also, a small application attack type can selectively affect certain company resources, sometimes in an undetectable way. These attacks usually do not have the purpose of interrupting the service but the misuse of resources that can lead to material losses.
We developed and implemented the system NAV AMS with the intention of solving all these problems.
Considering the facilities of the TCP protocol this means avoiding packet loss in the event of an attack. In order to avoid interruption of services, the notion of scrubbing was introduced in the mitigation process. If an attack is detected, the traffic to the targeted IP address is redirected to a high-capacity firewall that blocks malicious traffic, allowing only legitimate traffic to reach its destination.
There are of course also extreme cases where the attack reaches very high values and the decision of "blackholing" is taken. What makes the AMS system different from those implemented by other providers is the blocking of traffic intelligently, meaning that the transit to the affected destination will not be blocked on upstream links where there is no malicious traffic or there is the capacity to avoid congestion.
All these facilities contribute to the delivery of the highest quality service without interruptions and without worries.
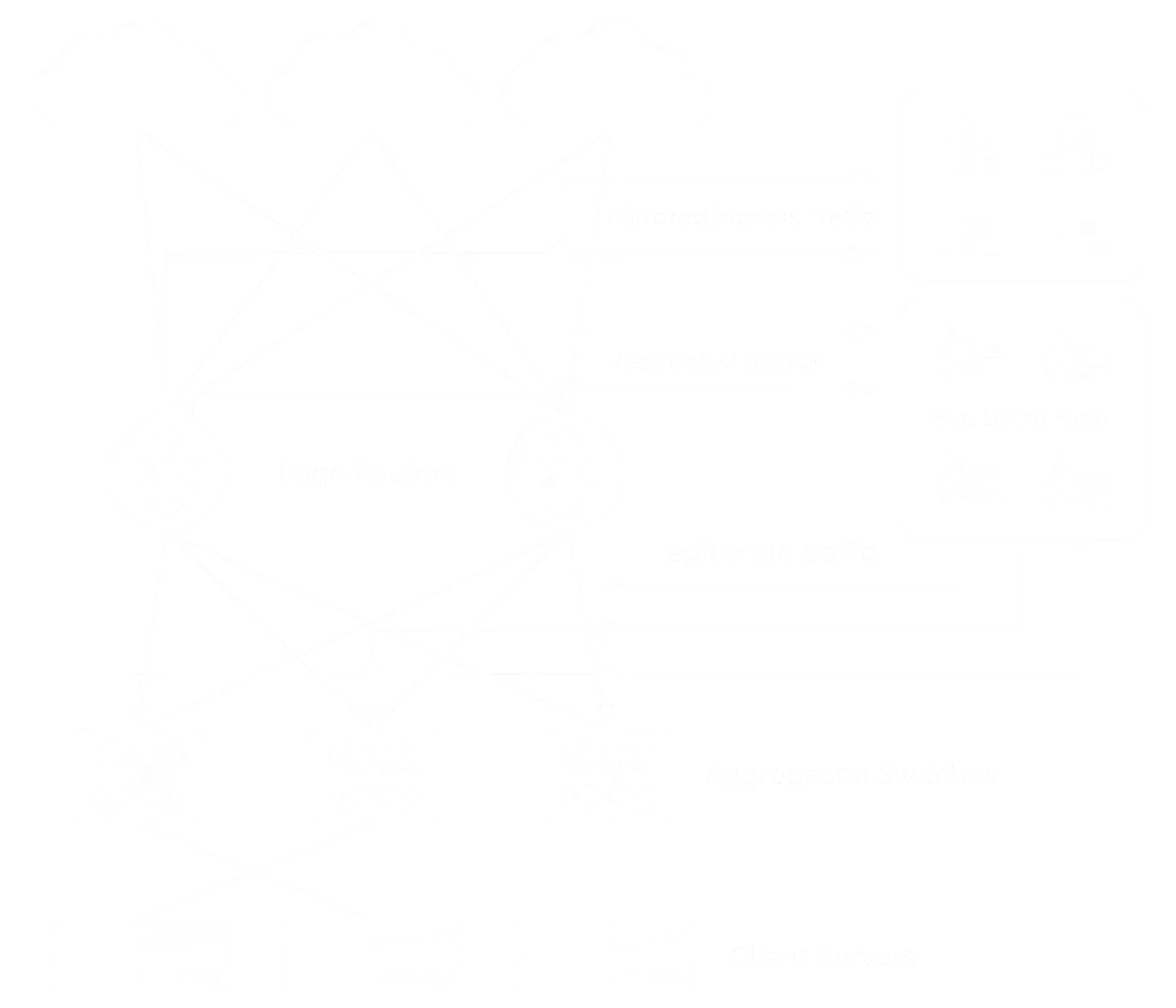
Attack detection is done using the TAP method, which means that all traffic entering the network is analyzed in real time and transparently.
The statistics are done at an interval of only 2 seconds which leads to a detection and mitigation time of maximum 3 seconds.
Total mitigation time: 3 seconds
The time elapsed from the start of the attack to its blocking.
Detection time: 2s
Block time: 1s
Reprobing interval: 1m*
* the interval at which the attack stopped/deactivated the filters.
Maximum scrubbing capacity:
140Gbps / 20Mpps
Types of mitigated attacks:
High pps / bw rate
TCP, UDP, ICMP, SYN Flood, Fragmentation, Application Flood.
Introduced latency: < 100μ (micro seconds)
Simultaneous casualties: 100,000
Simultaneous TCP connections: 128M (millions)
NAV AMS
NAV AMS system — Traffic analysis
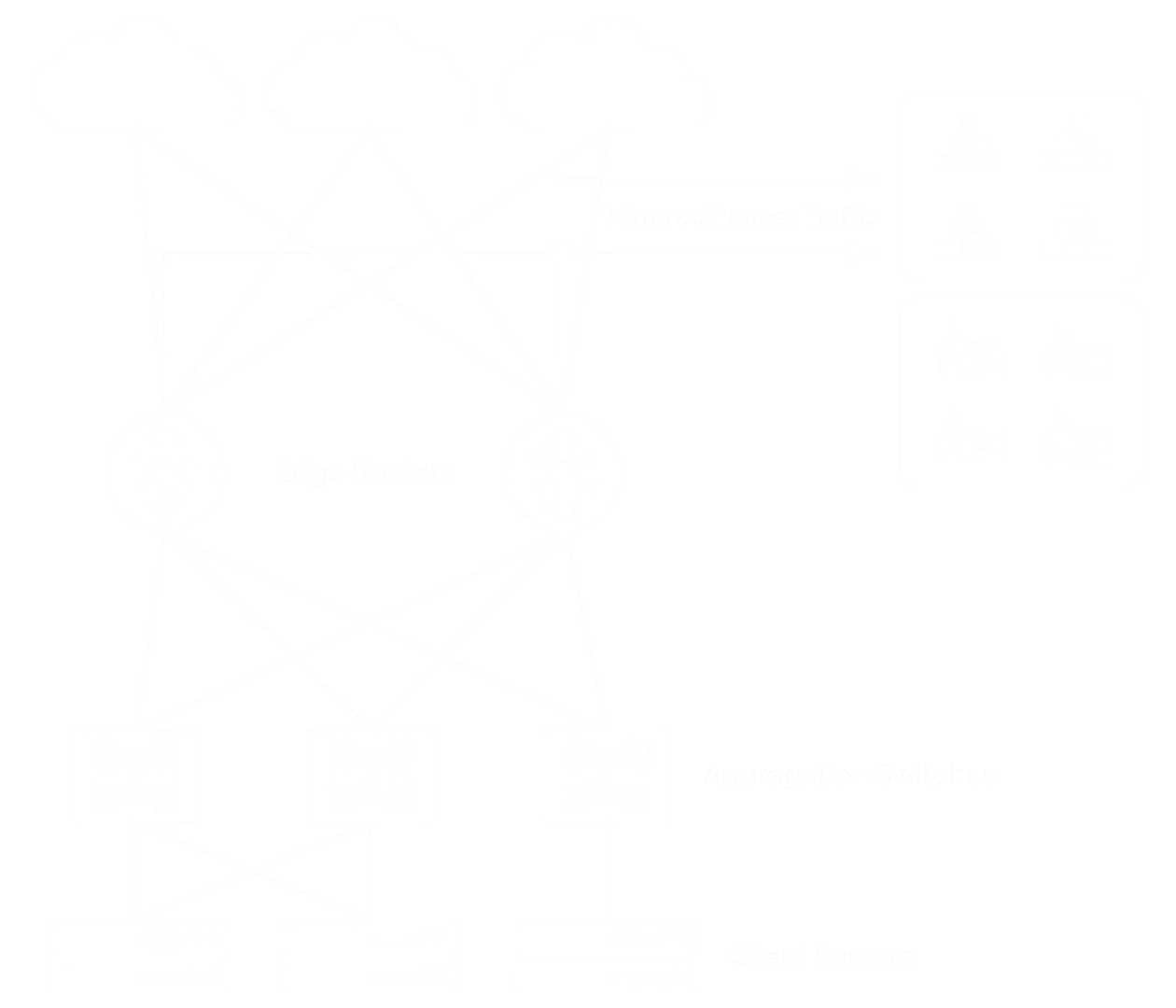
NAV AMS system — In action